- Category: machines
- Level: medium
- Points: 100
You’re given an entry point to a network, the goal is to pivot from the machine you logged into to another one on the network. First you’re going use ssh to connect to the target with the provided credentials on the challenge description.
After that type “ifconfig” to know your network details “ip, netmask, ..etc”.

You’ll find nmap installed so you’re going to use it to know which hosts are alive and how many ports are open. From the ifconfig output you’ll see two network adapters, i’ll just choose one to scan. After the scan finishes you’ll see a host running a Samba share server and the version is 4.6.3.After that we enumerate the shares and users of that server using nmap scripts.
nmap -p445 --script smb-enum-users,smb-enum-shares 172.30.0.3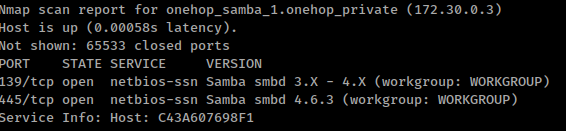

It looks like the server is accepting anonymous connections with READ/WRITE permissions. Now let’s see if there is a vulnerability for this version of the server.
searchsploit Samba 4.6
There a metasploit module for an rce vulnerability on that server, but the module won’t work with this server (probably because the server uses SMBv2 & the module uses SMBv1). Fortunately there is an exploit in this repo (https://github.com/opsxcq/exploit-CVE-2017-7494) clone it and install the requirements.
This exploit uploads a library to the share folder and then load it, then the library will listen on port 6699 once we connect to that port we will get a root shell.
Now we need to forward a port from our machine to the target network by using ssh. First we’re going to forward port 445 (needs root privileges) and the port 6699 (to connect to shell) note that we’ll forward the connection to the vulnerable server. by running :
ssh -N -L [LOCAL_PORT]:[REMOTE_IP]:[REMOTE_PORT] [HOST] -p[PORT]the -N options means no interact with the server.

Now using the exploit we will get our shell :
./exploit.py -t 127.0.0.1 -e libbindshell-samba.so -s myshare -r /home/share/libbindshell-samba.so -u guest -p guest -P 6699
Now we’re going to search for the flag file “root.txt” using “find” command
find / -name root.txt -type f 2>/dev/null
And we got the flag..